New Windows Defender Security Center features in Windows 10 Fall Creators Update
These are the most exciting features and improvements with the Windows Defender Security Center in the Windows 10 Fall Creators Update.
The Fall Creators update (version 1709) is finally available and gradually rolling out to millions of compatible PCs around the world. Along with all the new features and changes, this release also introduces new security enhancements — just in time to fight back the recent increase of malware and cyber attacks targeting Windows 10.
In this new version, Microsoft is focusing on making Windows 10 more secure against ransomware with "Controlled folder access," and it's attempting to help organizations, as well as regular users, to mitigate vulnerabilities before a patch becomes available through Windows Update with "Windows Defender Exploit Guard."
In this Windows 10 guide, we give you a closer look at the new features in the Windows Defender Security Center app included with the Fall Creators Update.
Controlled folder access
Starting with build version 1709, Windows Defender Antivirus introduces Controlled folder access, a feature designed to add an extra layer of security to protect your files against malicious programs and threats, such as ransomware.
When enabled, the new security feature monitors the changes apps make to your files stored in specific protected folders. If a blacklisted app tries to manipulate a file, controlled folder access will stop the attempt, and you'll get a desktop notification about the suspicious activity.
Windows Defender Antivirus protects the Documents, Pictures, Movies, and Desktop folders by default, which are locations that you can't change, but it's possible to include additional locations, such as from external hard drive, network shares, and mapped drives.
Although most of the apps you use on a regular basis will be allowed on your system, if one of those you trust gets blocked, Controlled folder access also includes an option to whitelist the app to enable it to make changes in the protected folders.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
Enabling Controlled folder access
Controlled folder access comes disabled by default, and you'll need to enable it manually, Navigate to Windows Defender Security Center > Virus & threat protection > Virus & threat protection settings, and turn on the Controlled folder access toggle switch.
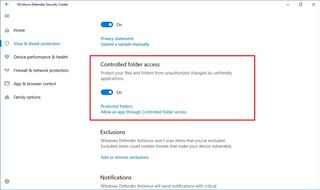
Adding new locations
If you need to add more locations to monitor, while in the Virus & threat protection settings, click the Protected folders link, and then click the Add a protected folder button to include new locations.
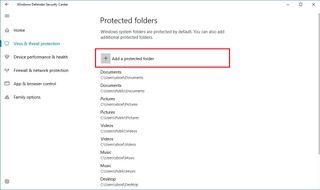
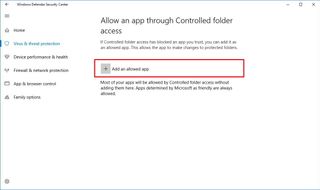
Whitelisting apps you trust
In the case that one of your trusted apps gets blocked, while on the Virus & threat protection settings page, click the Allow an app through Controlled folder access link, and then click the Add an allowed app button to add the executable for the app you want to allow.
This feature only works when Windows Defender Antivirus is your main security software; if you're running third-party antivirus on your machine, this feature won't be available.
Windows Defender Exploit Guard
Although security has always been a priority for Microsoft, before Windows 10 it took the company several years to release new versions of the OS, making the response to new threats very slow. In order to help commercial customers deliver mitigations against specific vulnerabilities, Microsoft created the Enhanced Mitigation Experience Toolkit (EMET), which allowed customers to keep devices secure without waiting until the next version of Windows.
However, because EMET was never part of Windows, and it was also limited in many ways, starting with the Fall Creators Update it is now possible to audit, configure, and manage system and app exploit mitigation settings within the Windows Defender Security Center app.
The best part is that you can take advantage of Windows Defender Exploit Guard settings even if you're running third-party antivirus.
Customizing exploit protections settings
Windows 10 ships with a configuration that will suit most users, but you can always customize the settings (as long as you know what you're doing) on Windows Defender Security Center > App & browser control > Exploit protection, and clicking the Exploit protection settings link.
Inside Exploit protection, you'll find two tabs, including "System settings" and "Program settings."
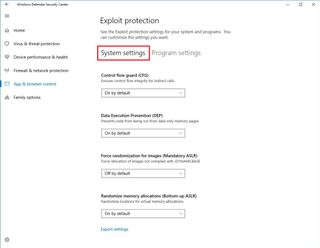
In the System settings tab, you can configure protection settings, including:
- Control Flow Guard (CFG) — Ensures control flow integrity for indirect calls.
- Data Execution Prevention (DEP) — Prevents code from being run from data-only memory pages.
- Force randomization for images (Mandatory ASLR) — Forces the relocation of images not compiled with /DYNNAMICBASE.
- Randomize memory allocations (Bottom-up ASLR) — Randomize locations for virtual memory allocations.
- Validate exception chains (SEHOP) — Ensures the integrity of an exception chain during dispatch.
- Validate heap integrity — Terminates a process when heap corruption is detected.
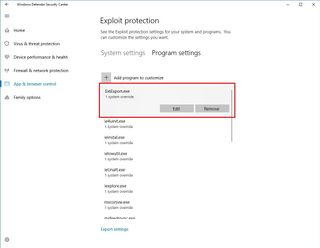
In the Program settings tab, you'll see a list of applications that are currently protected using the Exploit protection settings.
If you need to modify the current settings for a particular application, just select the executable from the list, and click the Edit button. Inside the page, you'll find some security features with an option to override system settings and set your own rules.
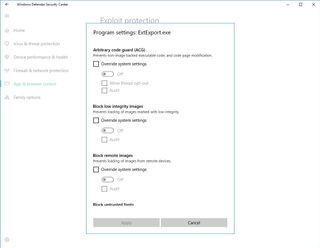
In this update, there are 21 different rules you can customize, some of which include:
- Arbitrary code guard (ACG) — Prevents non-images-backed executable code, and code page modification.
- Block low integrity images — Prevents loading of images marked with low-integrity.
- Block remote images — Prevents loading of images from remote devices.
- Block untrusted fonts — Prevents loading any GDI-based fonts not installed in the system Fonts directory.
- Code integrity guard (CFG) — Ensures flow integrity for indirect calls.
These settings are meant to add an extra layer of security against new threats even before they get an official fix through security patches or anti-malware solutions.
Windows Defender Advanced Threat Protection
We're just scratching the surface, and the Exploit protection settings on Windows 10 are part of a more complex topic. Microsoft is also adding more security enhancements to its Windows Defender Advanced Threat Protection (ATP) service for enterprise customers to create an antivirus using Microsoft's cloud-based security intelligence to detect infections faster than ever before.
In addition, Microsoft is now offering new tools, a security analytics view, and an updated detection dictionary to identify the latest attack techniques, which will enable network administrators to respond to attacks more quickly.
Initially, these security features will be available for commercial customers, but the company is looking into integrating Windows Defender ATP to the Windows Server platform and all customers in the future.
For more details about the Exploit protection settings, you can refer to the Microsoft Docs pages, and to learn about Microsoft's EMET, you can check out this Security TechCenter article.
Additional improvements and changes
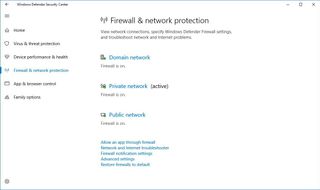
Another minor change can be found in the Firewall & network protection section of the Windows Defender Security Center dashboard, where you can now see more clearly which network profile is currently active. The page also lists firewall settings for domain networks.
On Windows 10 Enterprise, Microsoft is finally delivering Windows Defender Application Guard, which is a new feature that sandboxes web pages using Microsoft Edge to prevent internet malware and zero-day attacks from infecting your computer.
Windows Defender Application Guard was originally scheduled to release with the Creators Update, but it got pushed back, and now it's available with the Fall Creators Update.
Wrapping up
In this guide, we highlighted the new features and changes coming in the Windows Defender Security Center dashboard for the consumer version of Windows 10. Microsoft is also starting to offer a lot of additional features, but they're aimed at enterprise customers, such as Windows Defender Threat Protection and Windows Defender Application Guard.
More Windows 10 resources
For more helpful articles, coverage, and answers to common questions about Windows 10, visit the following resources:
- Windows 10 on Windows Central – All you need to know
- Windows 10 help, tips, and tricks
- Windows 10 forums on Windows Central
Mauro Huculak is technical writer for WindowsCentral.com. His primary focus is to write comprehensive how-tos to help users get the most out of Windows 10 and its many related technologies. He has an IT background with professional certifications from Microsoft, Cisco, and CompTIA, and he's a recognized member of the Microsoft MVP community.

